Brute Force Attack Tool For Mac
It contrasts MAC with hash functions or general encryption/decryption techniques and quantify the brute force attack difficulty for MAC and discuss the security requirements for MAC. The module also reviews two MAC implementations in Data Authentication Algorithm (DAA) and Cipher-Based MAC (CMAC), which are based on the use of block ciphers. A brute force attack tool for Mac OS. It’s open-source and has a mode that lets you perform attacks from multiple computers on the same password. It’s open-source and has a mode that lets you perform attacks from multiple computers on the same password.
A brute-force attack is considering as the most renowned method to crack the password. At the same, it’s not only to crack the password. Brute-force can also be used to identify pages and content hidden in a web application. This attack is basically “one try and hit” until you understand it correctly. However, keywords are always a serious threat to confidentiality and data integrity. Keywords of less than 7 characters are usually particularly sensitive to brute-force attacks. However, a series of incorrect commands or incorrect response responses (with attempts to recover or reuse) may indicate a collision of brute-force. The random attack involves guessing the password using various methods.
It is believed that brute-force attack is such a famous method for the password cracking by a few of the versions, it accounted for about 5.3% of definite security-breaches. However, it also encompasses the feature to guess the consumer name along with the passwords to get the illegal accessibility towards the system. Though, brute force attack is the simplest method to attack along with a very high rate of success. All the same, efficiency depends on a predefined value. If it’s bigger, it’ll last longer, but it’s more likely to work.
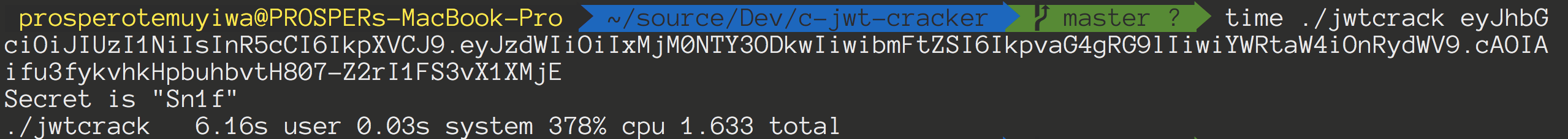
- A brute force attack is a popular cracking method: by some accounts, brute force attacks accounted for five percent of confirmed security breaches. A brute force attack involves ‘guessing’ username and passwords to gain unauthorized access to a system.
- A brute force attack tool for Mac OS. It’s open-source and has a mode that lets you perform attacks from multiple computers on the same password. This makes the password guesser even faster.
- These tools essential analyze logs using regular expressions. Hackers have found ways around both of these tools in the past. Lastly, you have a great tool to block ssh brute force attacks right on your server: IPtables. Using IPtables to Stop SSH Brute Force Attacks. I like to think of this approach similar to flow rates with pipes.
On the other side of the coin, the most common and easy-to-understand example of an attack on brute force is a dictionary for cracking a password. In this case, however, the attacker uses a password book that contains a million words that can be used as a password. Though, the attacker then tries to confirm the password individually. However, this traditional technology lasts longer if the password is long enough.
It is considered that the several technologies which are supposed to associate with password break actions are known as reverse brute – force. However, it is taking a reverse line of attack to crack the passwords. Here, the attacker is trying a single password on several usernames. Give a thought that you are made aware with the password but you don’t have a guess regarding usernames. In that scenario, you would keep trying the similar password and make predictions of other usernames while waiting for the best combination to work. You have an option to make use of it in different sites, protocols and software, that won’t block the requests once it gets some of the void trials.
Here we come up with some of the most famous brute-force tools that crack the password.
L0phtCrack
L0phtCrack seems to be popular for the capability of password cracking in the Windows. It utilizes rainbow-tables, hybrid-attacks, brute force, and dictionary. The topmost noteworthy aspects of the L0phtcrack are the multi-processor algorithms, extraction of hash from the sixty-four bit Windows forms, scheduling, decoding and monitor the network. If a person is interested to keep cracking the password of the Windows system then it is recommended to try L0phtCrack.
Hashcat
Hashcat is claiming to be the quickest tool to crack the password that is CPU based. It’s also free of cost tool, and it comes for the platforms of Mac OS, Windows and Linux. This tool is supporting numerous algorithms of hashing. It is supporting numerous attacks that include Toggle-Case-attack, Table-Lookup-attack, Fingerprint-attack, Rule-based-attack, Mask-attack, Hybrid-attack, Permutation-attack, Dictionary-attack, Combinator-attack and Brute-Force-attack.
John – the – Ripper
John – the – Ripper is another amazing device that doesn’t need to be introduced. Organizing attacks has long been a favourite option. Later, developers sent it from several other systems. Allows you to enter a weak password or break a password to abort the confirmation. You can also run it to store encrypted passwords.
Rainbow Crack
Brute Force Attack Tool For Mac Download
It creates a rainbow board for use in an attack. That is how it differs from other traditional rough tools. Rainbow maps are read aloud. It helps reduce the time required to complete the attack. To save time, you can take these rainbows and use them in attacks.
Cain and Abel
We’re sure you have heard the name of this hacker before. It should be noted that some antivirus scanners recognize this as malware. It uses vocabulary, beast power, hybrid attacks and rainbows.
Ophcrack
It would crack the password of Windows by make use of L-M-hashes via the rainbow tables. It’s free of cost as well as an open-source tool. In many scenarios, this tool would crack the Windows password within an hour.
SAMInside
SAMInside considered as another famous tool to crack the passwords of Windows OS. However, it’s comparable to the tools of Lophtcrack and Ophcrack. It is claiming that it would crack approx. ten million passwords on every second as well as support more than four hundred hashing algorithms.
DaveGrohl
This password cracking tool is the most renowned brute-forcing-tool for the Mac-OS X. DaveGrohl is supporting the entire accessible versions of the Mac-OS X. It also supports incremental attacks as well as dictionary attacks. Now it’s become an open-source, so here you have access to download source-code.
Ncrack
This password cracking tool is also much known to crack the network authentications. Ncrack is supporting numerous protocols that include telnet, FTP, pop3(s), SMB, HTTP(s), VNC, SSH, and RDP. It allows keeping performing several attacks that comprise brute-forcing-attacks.
Brute Force Attack Tool For Mac Pro
However, it has been determined that brute force is considering as the strongest way to destroy a password. That’s why we talk about strong passwords; users typically recommend using long passwords with lowercase letters, uppercase letters, numbers, and special characters. It does not make the use of brute force impossible but makes it more difficult. Therefore it takes a long time to get the password for your hard drive. Moreover, obtaining information security certifications also helps in dealing with the security concerns. Almost every hash algorithm uses bold force to guess and test. This attack is best if you have offline data access. In this case, it facilitates cracks and prolonged use. The best way to prevent it – is to limit invalid links.
I am Daisy Bell and a pro-level blogger with years of experience in writing for multiple industries. I have extensive knowledge of Food, Fitness, Healthcare, business, fashion, and many other popular niches. I have post graduated in arts and have keen interest in traveling.
- Advertisement
- Brutezip v.0.12A shell script which determines by bruteforce the best compression format (bzip2, gzip, Z, zip, etc.) and which compression level to use in order to archive a file the smallest ...
- FileHashler v.0.1.0Java based API and commandline utility for cross-platform file encryption and archivation (up to 2,1 GB). Uses Twofish and SHA-256 *** due to current design error FHL has a weakness to bruteforce attacks and usage is deprecated!!
- HTTPBrute v.1.00HTTPBrute is used to calculate HTTP Digest Access Authentication as per RFC 2617. The tool will be able to perform bruteforce attacks to retrieve a lost password for a given Authentication response. MD5 is the only hashing algorithm ...
- HumanSudokuSolver v.0.1HumanSudokuSolver is intended to solve Sudoku puzzles in a way human beings would do (non bruteforce). It currently solves most of the puzzles I tried and can output a step-by-step solution. Developers who want to contribute are ...
- PseudoQ v.0.9.0A java application for creating, playing and solving SuDoku puzzles of various types. Features both a Swing GUI and command-line operation. The automatic solving of puzzles uses 'smart' techniques rather than a bruteforce search of every ...
- Ukodos v.0.0.2A non-brute-force sudoku solver. Ukodos is sodoku backwards; According to wikipedia, Sodoku is a bacterial zoonotic ...
- Aorta p2p Tasklet cluster v.rcGeneric clustering/load-balancing platform (over a LAN or internet) using java based P2P Aorta workers that execute java 'tasklets'. Various tasklets can be implemented to solve fractals, process images, render webpages, crack RSA 'brute ...
- AirGrab Password PRO v.1.0.39The AirGrab Password PRO allows you to create random passwords that are highly secure and extremely difficult to crack or guess due to an optional combination of lower and upper case letters, numbers and other symbols.
- AirGrab Password v.1.0.37The AirGrab Password allows you to create random passwords that are highly secure and extremely difficult to crack or guess due to an optional combination of lower and upper case letters, numbers and other symbols.
- System Cleaner for Mac v.1.2.7Mac Cleanse helps you cover your tracks by quickly and easily removing recent file history, chat logs, caches, cookies, web site history, and more!
- Websiteoutlook V PHP Clone Script v.2Step by Step Installation New Comment System (using Disqus.com) Generate Social Bookmark Link Details Get Website server Info Website Hosting Server City, Country detail Alexa Ranks (Improve) Pagerank (improved) DMOZ Directory Display MyWot ...
- SoftPerfect WiFi Guard v.2.1.2A specialised network scanner that helps to protect and keep your WiFi network secure. It scans your wireless network at set intervals and alerts you immediately if it has found any new or unknown connected devices that could belong to an intruder.
- Force Quit all Applications for Mac OS v.1.0Force quit all open applications Now! This small app will force quit all applications, helpful if your system is having trouble, or you need to quickly close all open applications.
- G-Force v.3.9.2G-Force 3.9.2 is a feature-rich and trustworthy audio visualization plug-in for media players and can also visualize auxiliary or 'line-in' audio.G-Force features fast anti-aliased effects, millions of possible effect combinations, savable and ...
- 4st Attack v.2.1.44st Attack is a gorgeous looking connect-four. And whilst being good looking it's scarily ...
- Block Drop Attack v.1.0A falling block puzzle game. Very similar to the game Crack-Attack, but with speed and extensibility in ...
- Penguin Attack v.rcPenguin Attack is a puzzle game in the style of Tetris ...
- Attack of the Paper Zombies for Mac OS v.1.2A strategy game where your small band of space marines hold off and defeats a giant horde of alien zombies. Even though there are hundreds more enemies than your soldiers, you have some aces up your sleeve. You can construct automated guns and ...
- Space Attack! v.rcThis is a very simple game i made on school for a project. Comments are totally ...
- Ultimate Maths Invaders for OS 9 v.1.0The new, fun spaceattack math's game that drills number facts and tables. 10 challenge levels allow pupils to test themselves using preset content combinations. Features Cool, exciting 3D-style graphics and wide ranging content for ages 5-14+.
Brute Force Attack Tool For Mac Os
- SoftPerfect WiFi Guard A specialised network scanner that helps to protect and keep
- Titan Attacks for Mac OS The Earth is under attack from evil aliens from Titan!
- AirGrab Password PRO The AirGrab Password PRO allows you to create random
- G-Force G- Force 3.9.2 is a feature-rich and trustworthy audio
- Note Gate 2 for Mac OS A real-time pitch-based Audio Unit volume filter effect.
- AirGrab Password The AirGrab Password allows you to create random passwords
- Get Your Data Back GetDataBack will recover your data if the hard drive's
- Attack of the Paper Zombies for Mac OS A strategy game where your small band of space marines hold
- System Cleaner for Mac Mac Cleanse helps you cover your tracks by quickly and
- Websiteoutlook V PHP Clone Script Step by Step Installation New Comment System (using